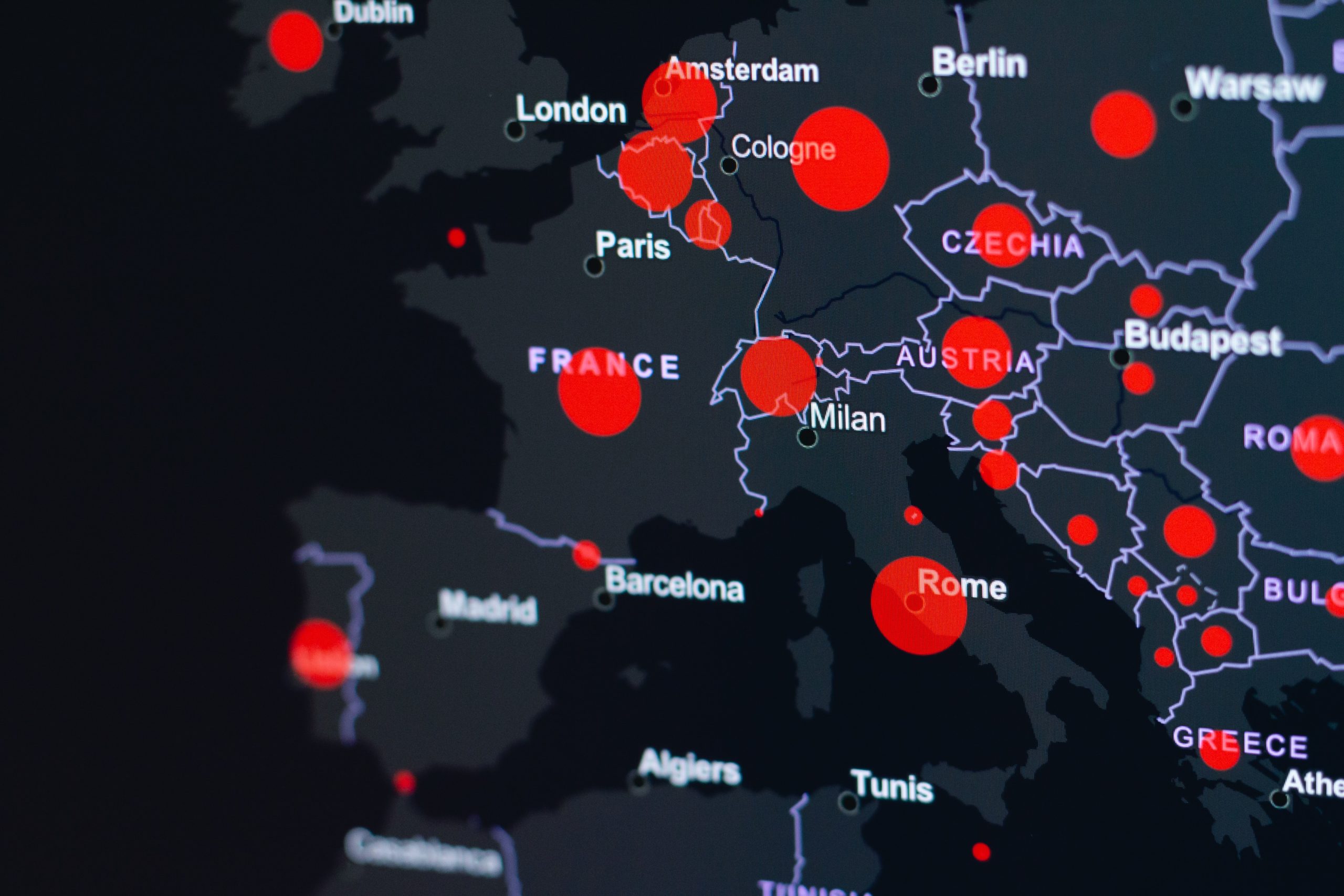
Intrusion Detection Systems

Intrusion Detection Systems are one of the most critical security components, covering methods that monitor the activities on the network and analyze the traffic to detect possible attacks, violations, and threats. On the other hand, intrusion prevention systems are network security systems that cover the detection and prevention of seizures.
Today, at the same time, these complex network systems can no longer be protected only with encryption or firewall; realities such as network traffic are constantly mat monitored. Hence, made accurate–time detection of attack attempts is inevitable.
These systems can also reveal weaknesses in the security policies of companies and institutions. Furthermore, intrusion prevention systems also detect the information gathering activities of the attackers about the network and prevent the attackers from getting information about the plans. Therefore, they can also stop it at this stage.
Intrusion Detection and Prevention Systems should be strategically positioned within the network against network attacks. Thus, any attack or abnormal network traffic can be detected quickly. The detection and response teams can take the necessary measures to cyber incidents before the incidents grow.

- Intrusion Detection System (IDS)
It creates and sends alarms on itself, detects violations, and blocks source traffic.
- Intrusion Prevention System (IPS)
This system enables the production of more detailed alarms and records through a cyber incident management system installed on the network, enabling the detection and response teams to monitor and attack in more detail and take precautions against cyber threats.
Common Detection and Prevention Techniques
- Signature Based Technique
This system proceeds through comparing signatures with observed events to identify possible events. An alarm is generated if there is a successful match.
- Anomaly Based Technique
An intrusion detection and prevention system using anomaly–based techniques have profiles that represent the expected behavior of users, hosts, network, and applications.
- Stateful Protocol Analysis Technique
Stateful protocol analysis compares generally accepted definitions of correct protocol activity with observed events for each protocol state.
- Intrusion Detection System with Machine Learning
In Machine Learning, classification algorithms learn the output from the given training set inputs and then try to correctly classify the test data for which the class is uncertain.
The KDD–99 dataset is widely used for intrusion detection. This dataset includes a wide variety of attacks simulated on a military network.
There are Denial of Service (DoS), Probe, User to Root (U2R), Remote User (R2L) attacks in the data set.
- Denial of Service (DoS): A denial of service attack is a malicious person, computer, or device that interrupts the operation of the device and renders it inaccessible to users.
- Remote User (R2L): The attacker gains local access due to the attack by gaining unauthorized access.
- User to Root (U2R): It raises the user rights that provide local access to the high privilege user.
- Probe: The attacker’s attempt to obtain information about the victim machine.




